[Top] [Prev] [Next] [Bottom]
With a ChoiceNet server you can create lists of sites to provide custom access for dial-in and network users. You can create filters that use one or more of these lists to permit or deny user access.
ChoiceNet lets you centralize the storage of packet filters. Packet filters can control inbound or outbound traffic for each interface and user. You can apply filters to users, locations, or interfaces as either input or output filters. You can filter packets for TCP, UDP, and ICMP protocols.
This chapter includes the following topics:
This section describes how to construct site lists to customize user access, and provides several examples that explain how to use them.
ChoiceNet site lists are simple text files that you create and store in the /etc/choicenet/lists directory on the ChoiceNet server. The filename is the list name and consists of up to 15 printable, nonspace, ASCII characters. ChoiceNet lists can be created or modified at any time.
The site list contains the IP address-in dotted decimal notation-or the hostname of sites. Any number of sites can be included in a list. The site list file must have only one hostname or IP address per line. A simple site list appears in Figure 5-1.
Figure 5-1 Example Contents of wwwok, a Simple ChoiceNet Site List
homeserver.edu.com
www.site1.com
www.site2.com
www.site3.com
192.168.247.55
172.16.240.3
serverx.edu.com
|
Group sites in a list according to the purpose of the list.
Preventing Access. If you want to prevent access to certain sites by network or dial-in users, you can place those sites together in one list. You can give this list any name, as long as the name meets the naming requirements-for example, deny_list or no_go.
Allowing Access. If you want to specify certain sites that users are expressly permitted to access, you can place those sites together in another list. You can give this list any name, as long as it meets the naming requirements-for example, wwwok or permit_list.
To use a list in a filter rule, prefix the list name with an equal sign (=) as shown in Figure 5-2. See "Constructing ChoiceNet Filters" on page 5-7 and Appendix B, "Defining Filter Rules," for information about filter rules. You can use a site list for either the source or destination address in a rule, but not for both addresses in the same rule.
Figure 5-2 Example Filter Rule Using a Site List
permit 172.16.0.0/16 =wwwok tcp dst eq 80
|
When a connected user attempts to access a site, the PortMaster evaluates the request against the applied filter, starting at the first rule and continuing until it finds a rule that matches. If the rule includes a site list, the PortMaster determines from the ChoiceNet server whether the requested site is in the site list.
You must run the ChoiceNet buildlist utility if you add or change any lists in the /etc/choicenet/lists directory. This utility resolves any site names included in the lists to their IP addresses and constructs a DBM database of the resolved addresses. The structure of a DBM database enables the server to find IP addresses quickly.
To resolve the names for a specific list, run the utility on the server as follows:
/etc/choicenet/buildlist ListName
|
To resolve the names for all lists that have changed since the last time buildlist was run, run the utility as follows:
The ChoiceNet server uses the Domain Name System (DNS) for the Internet and the Network Information Service (NIS) for intranets to resolve names to addresses when you run /etc/choicenet/buildlist. The utility formulates a query for each name in a list in the /etc/choicenet/lists directory and sends the queries to a local domain name server. The name server translates the names to addresses and returns those to the ChoiceNet server. More information on DNS can be found in DNS and BIND in a Nutshell by Albitz and Liu.
The utility creates a DBM database in the /etc/choicenet/lists.dbm directory. Depending on your system, the database will consist of one of the following:
Note:
 If name resolution fails and you want to rebuild the list, the DBM file(s) for the
list must first be deleted.
If name resolution fails and you want to rebuild the list, the DBM file(s) for the
list must first be deleted.
Suppose your /etc/choicenet/lists directory contains the lists shown in Figure 5-3.
Figure 5-3 Sample Contents of the /etc/choicenet/lists Directory
-rw-------
| 1
| root
| other
| 200
| Jan 30
| 11:59
| wwwok
|
-rw-------
| 1
| root
| other
| 105
| Jan 30
| 12:14
| deny_list
|
In this example, assume that on your system buildlist generates .dir and .pag DBM files instead of .db DBM files. The first time you run buildlist, it generates the files shown in Figure 5-4.
Figure 5-4 Sample Contents of the /etc/choicenet/lists.dbm Directory
-rw-------
| 1
| root
| other
| 0
| Jan 30
| 12:25
| wwwok.dir
|
-rw-------
| 1
| root
| other
| 2048
| Jan 30
| 12:25
| wwwok.pag
|
-rw-------
| 1
| root
| other
| 0
| Jan 30
| 12:25
| deny_list.dir
|
-rw-------
| 1
| root
| other
| 1024
| Jan 30
| 12:25
| deny_list.pag
|
A few days later, suppose you modify the deny_list file and add two new lists, no_go and permit_list, as shown in Figure 5-5.
Figure 5-5 Sample Modified Contents of the /etc/choicenet/lists Directory
-rw-------
| 1
| root
| other
| 200
| Jan 30
| 11:59
| wwwok
|
-rw-------
| 1
| root
| other
| 200
| Feb 4
| 08:24
| deny_list
|
-rw-------
| 1
| root
| other
| 95
| Feb 4
| 08:56
| no_go
|
-rw-------
| 1
| root
| other
| 190
| Feb 4
| 09:08
| permit_list
|
When you run buildlist now, it updates and generates the files as shown in Figure 5-6.
Figure 5-6 Sample Modified Contents of the /etc/choicenet/lists.dbm Directory
-rw-------
| 1
| root
| other
| 0
| Jan 30
| 12:25
| wwwok.dir
|
-rw-------
| 1
| root
| other
| 2048
| Jan 30
| 12:25
| wwwok.pag
|
-rw-------
| 1
| root
| other
| 0
| Feb 4
| 12:25
| deny_list.dir
|
-rw-------
| 1
| root
| other
| 2048
| Feb 4
| 12:25
| deny_list.pag
|
-rw-------
| 1
| root
| other
| 0
| Feb 4
| 12:25
| no_go.dir
|
-rw-------
| 1
| root
| other
| 1024
| Feb 4
| 12:25
| no_go.pag
|
-rw-------
| 1
| root
| other
| 0
| Feb 4
| 12:25
| permit_list.dir
|
-rw-------
| 1
| root
| other
| 2048
| Feb 4
| 12:25
| permit_list.pag
|
The files wwwok.dir and wwwok.pag are not updated because their modification dates (Figure 5-4) are more recent than that of the wwwok file (Figure 5-5). The modification date of the deny_list file (Figure 5-5) is more recent than that of the files deny_list.dir and deny_list.pag (Figure 5-4), so buildlist updates these files. The other two files are new, so buildlist generates directory files to resolve the included names.
Packet filters can limit certain kinds of internetwork communications by permitting or denying the passage of packets through network interfaces. By placing well-written rules in the appropriate sequence within a filter, you can control access to specific hosts, networks, and network services.
Packet filtering analyzes the header information contained in each packet sent or received through an interface. The header information is evaluated against a set of rules, which either allow the packet to pass freely through the interface or cause the packet to be discarded without being forwarded.
ChoiceNet passes the packet to permit access to a service or site, and discards a packet to deny access to a service or site. This process reduces network traffic and provides more immediate feedback to a user attempting unauthorized access.
Each interface, whether synchronous, asynchronous, or Ethernet, can have a customized set of rules. For dial-in and dial-out interfaces, packet filters are enabled when a connection becomes active on the port (the port status on the PortMaster transitions to ESTABLISHED). For an Ethernet interface, filters are enabled as soon as the name of the input or output filter is applied to the interface.
You can apply input filters, output filters, both input and output filters, or no filters to a user, location, or interface. The terms input and output are defined relative to the PortMaster.
Use an input filter to filter packets coming into a PortMaster on an interface. Use an output filter to filter packets going out of a PortMaster on an interface. Figure 5-7 shows examples of how to apply input and output filters for a network using an Office Router to access the Internet through an Internet service provider (ISP).
Figure 5-7 Examples of Input Filters and Output Filters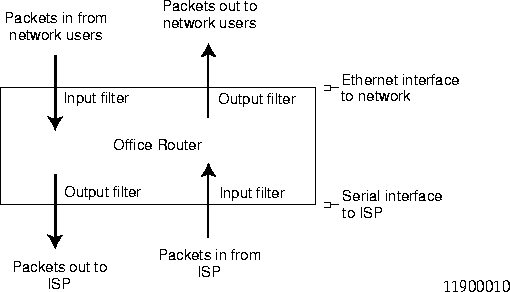
Packets can be filtered according to the following attributes:
You can create or modify ChoiceNet filters at any time, independent of any active packet filters. To use centralized storage and dynamic downloading for ChoiceNet filters, place the filters in the /etc/choicenet/filters directory on the ChoiceNet server. Each filter consists of a text file with the same name as the filter.
You can define input and output filters for Ethernet interfaces, hardwired serial ports, users, and locations. When ChoiceNet is used with RADIUS (the typical application), you can specify filters in user entries on the RADIUS server.
You can associate filters with network users configured for dial-in SLIP or PPP access. When the user makes a PPP or SLIP connection, the designated filters are applied to the interface used.
You can associate location filters to dial-out locations using SLIP or PPP connections. When the connection is established to a remote site, the designated filters are applied to the interface used.
Because filters are very flexible, you must carefully evaluate the types of traffic that a specific filter permits or denies through an interface. If possible, test filters to verify that the filter is operating as you intended. The log keyword is very useful when you are testing and refining filters.
Note:
 Any packet that is not explicitly permitted by a filter rule is denied. However,
an empty filter permits everything. If you create a filter and apply it without defining
any rules, the filter will permit all packets.
Any packet that is not explicitly permitted by a filter rule is denied. However,
an empty filter permits everything. If you create a filter and apply it without defining
any rules, the filter will permit all packets.
When creating filters for use with ChoiceNet, follow these guidelines:
Placing rules in the order you want them evaluated eliminates ambiguity about how a packet is handled. The first rule that matches the packet is applied. If the rule is a permit statement, the packet is passed. If the first matching rule is a deny statement, the packet is discarded. If the packet does not match any of the rules, the packet is discarded.
In addition, specify packets that represent the highest volume of traffic early in the list of rules, where possible. Give careful consideration to which services and sites are permitted or denied for which users or interfaces.
ChoiceNet filters are simple text files that the system administrator creates in the /etc/choicenet/filters directory. The filename is the filter name and consists of up to 15 printable, nonspace ASCII characters.
RADIUS requires that filter names must end with .in for input filters and with .out for output filters. However, you must omit the suffix from the filter name in the Filter-Id reply item in the RADIUS user entry. The PortMaster appends .in for the input filter and .out for the output filter when it applies the filter to the user.
The filter file contains the rules to be followed when the filter is applied. You define the rules with keywords and values as described in Appendix B, "Defining Filter Rules."
You can add comments to the filter by beginning each comment line with a number sign (#). Comments can be useful as the number of filters you administer increases.
Consider the example filter net.in. Figure 5-8 shows the contents of this simple filter with seven rules as stored in /etc/choicenet/filters/net.in.
Figure 5-8 Simple ChoiceNet Filter
#
#These are comment lines you can use to describe
#what this filter does or who it is for.
#
permit tcp estab
permit udp dst eq 53
permit tcp dst eq 53
permit tcp dst eq smtp
permit 0.0.0.0/0 =wwwok tcp dst eq 80
deny tcp dst eq 80 log notify
permit 0.0.0.0/0 =mailbox tcp dst eq 110
|
Table 5-1 describes each rule of the net.in filter.
When a ChoiceNet server is used with RADIUS, the ChoiceNet filters are associated with individual users in the RADIUS user entry. Each entry consists of a username, check items to authenticate the user, and reply items that provide information about the user and specify what that user can do. Filter-Id is a reply item that identifies the filter to be associated with that user. In the user entry shown in Figure 5-9, an input filter named user.in and an output filter named user.out will be applied to user bob when he connects.
Figure 5-9 RADIUS User Entry Specifying a Filter
bob Password = "ge55gep"
Service-Type = Framed-User,
Framed-Protocol = PPP,
Framed-MTU = 1500,
Filter-Id = "user"
|
Do not specify the .in and .out suffixes in Filter-Id. When a user attempts access, the PortMaster appends the appropriate suffix to the filter name provided by RADIUS.
The PortMaster first looks for each filter in its local Filter Table. If it does not find the filter there, and a ChoiceNet server has been set, the PortMaster sends a request to the ChoiceNet server to download the filter.
An ISP can use ChoiceNet to offer special services to its subscribers. The ISP can customize access to sites or services for groups of subscribers that share similar interests. One group might be interested in access only to the Web, another in access to role-playing games, another only in sites that are church-related, and another only in sites that relate to business and economics.
This example shows how an ISP might offer a custom service for individual subscribers to provide access only to Web sites suitable for children (Figure 5-10). In this example, the ISP takes advantage of Yahooligans, a service available from Yahoo, Inc., and distributed with ChoiceNet. Yahooligans is a guided service for the Web designed specifically for children ages 8 through 13.
Figure 5-10 ISP Providing Custom Access for an Individual Subscriber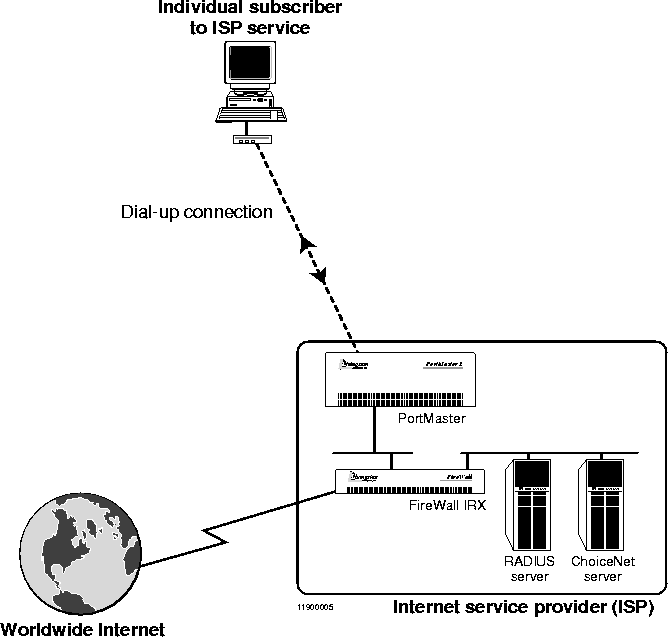
Figure 5-11 shows an example of a preconfiguration worksheet containing all the information needed to configure ChoiceNet for this example. Appendix D, "Preconfiguration Worksheets," has blank worksheets you can use to collect information before installing and configuring ChoiceNet.
Figure 5-11 Preconfiguration Worksheet for Example 1 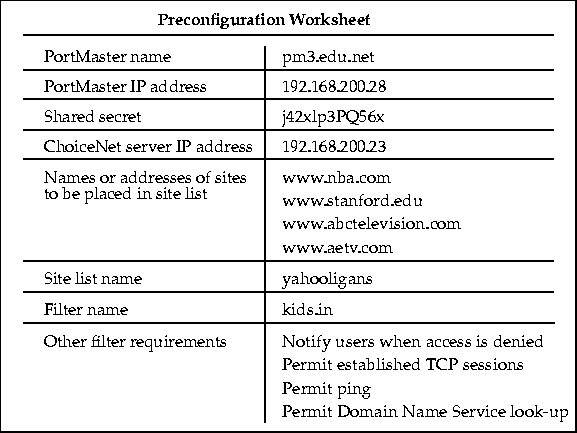
Follow these steps to configure ChoiceNet to limit child access (Example 1):
1. Establish the ChoiceNet service in the /etc/services file on the ChoiceNet server:
choicenet 1647/udp filterd
|
2. On the ChoiceNet server in the /etc/choicenet/clients text file, do one of the following, but not both:
-
Define a ChoiceNet client name and shared secret:
#Client Name Shared Secret
#-------------------------------------------
pm3.edu.net j42xlp3PQ56x
|
-
Define a ChoiceNet client IP address and shared secret:
#Client Name Shared Secret
#-------------------------------------------
192.168.200.28 j42xlp3PQ56x
|
3. On the PortMaster, specify the address of the ChoiceNet server and define the shared secret:
Command> set choicenet 192.168.200.23
Command> set choicenet-secret j42xlp3PQ56x
Command> save all
|
4. Create the /etc/choicenet/lists/yahooligans file on the ChoiceNet server:
www.nba.com
www.stanford.edu
www.abctelevision.com
www.aetv.com
|
The list contains the Yahooligans-provided sites, one per line. The list is much abbreviated in this example.
5. Resolve the names in the yahooligans list:
/etc/choicenet/buildlist yahooligans
|
6. Create the /etc/choicenet/filters/kids.in filter on the ChoiceNet server for the custom Yahooligans access:
permit tcp estab
permit udp dst eq 53
permit tcp dst eq 53
permit 0.0.0.0/16 =yahooligans tcp dst eq 80
permit icmp
deny log notify
|
7. Install the user notification pop-up on each user's PC or Macintosh, if desired.
Refer to Chapter 4, "Installing User Notification."
8. Associate the kids.in filter with individual users on the RADIUS server.
To associate the filter with user joey for example, define the Filter-Id reply item in joey's RADIUS user entry as the filter name, stripped of the suffix .in:
joey Auth-Type = System
Service-Type = Framed-User,
Framed-Protocol = PPP,
Framed-Address = 255.255.255.254,
Framed-Routing = None,
Framed-MTU = 1500,
Filter-Id = "kids"
|
When joey dials in to the PortMaster, RADIUS will apply the kids.in input filter on the interface coming into the PortMaster from the user.
9. Start the filter daemon using the following command:
With this ChoiceNet filter in place, subscribers to the Yahooligans service can gain Web access to only the sites that are specified in the yahooligans list. The subscribers can only use DNS, HTTP, and ICMP services.
When a subscriber to this service attempts to connect to a site that is not listed in the yahooligans list, or tries to access a service not listed, such as FTP, the notify keyword in the rule opens a pop-up window on the subscriber's computer to inform the subscriber that access is denied. Because of the log keyword in the rule, the failed access attempt is also logged to the auth.notice facility of the client's loghost.
In this example, an ISP also uses the Yahooligans service to provide custom access to the Web. A school needs Web access for its students, but wants to ensure that they only access sites suitable for children (Figure 5-12). The ISP uses a filter to specify the yahooligans site list and deny students access to sites not in the list.
Figure 5-12 ISP Providing Custom Access for a School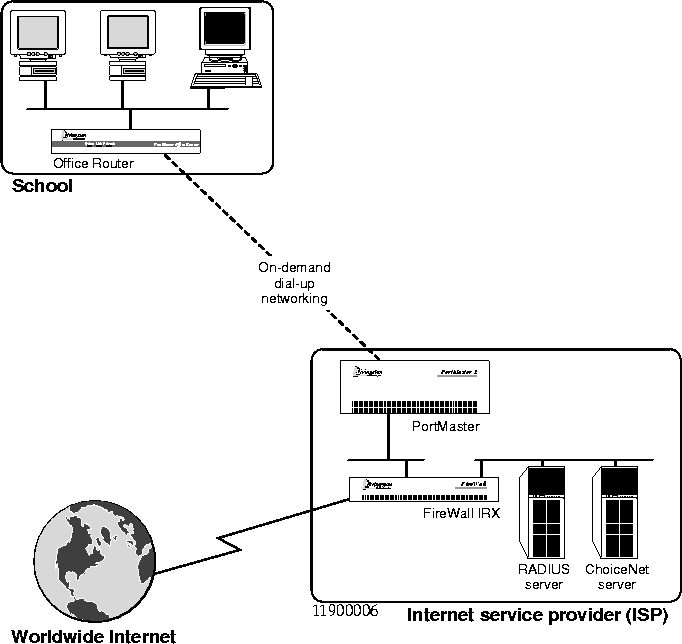
ChoiceNet cannot download filters dynamically on the interface used to reach the ChoiceNet server. In this example, the school uses on-demand dial-up networking to connect to the ISP and the ChoiceNet server. If the filter is applied on an interface at the school, the ISP cannot use the centralized filter storage feature of ChoiceNet. In this case, the filter must be stored in the Filter Table on the school's Office Router.
The ISP can apply filters at one or more interfaces to limit access by students at the school. Figure 5-13, Figure 5-14, and Figure 5-15 show several alternative methods.
School's Ethernet Interface. Figure 5-13 shows an input filter students.in and an output filter students.out applied on the Ethernet interface of the school's Office Router. The students.in filter evaluates packets coming into the Office Router from students on the school network. The students.out filter evaluates packets going out from the Office Router to students on the school network.
Figure 5-13 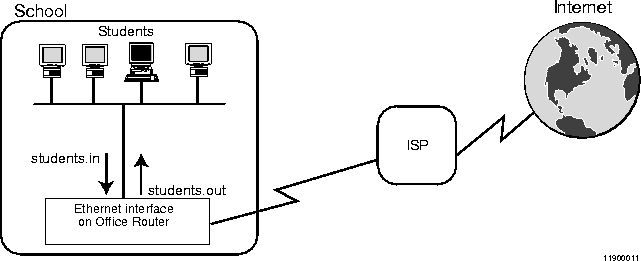 Filters Applied on the School's Office Router Ethernet Interface
Filters Applied on the School's Office Router Ethernet Interface
School's Serial Interface. Figure 5-14 shows an input filter internet.in and an output filter internet.out applied on the serial interface of the school's Office Router. The internet.in filter evaluates packets coming into the Office Router from the Internet. The internet.out filter evaluates packets going out from the Office Router to the Internet.
This configuration cannot be used with a dynamically downloaded file, but can be used with a site list.
Figure 5-14 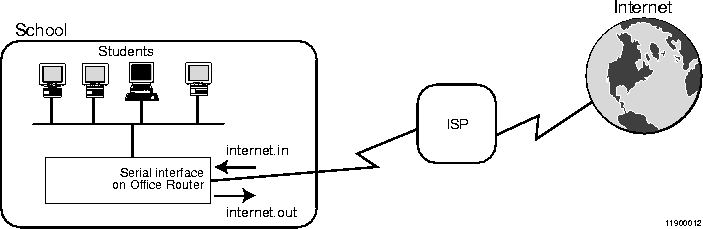 Filters Applied on the School's Office Router Serial Interface
Filters Applied on the School's Office Router Serial Interface
ISP's Serial Interface. If the ISP is providing this service to a number of schools, storing the filters on the ChoiceNet server makes the filters easier to administer. Each filter can be stored on the ChoiceNet server and applied to an interface on the PortMaster at the ISP.
In Figure 5-15, the ISP has applied an input filter kids.in on the interface coming into the ISP's PortMaster from the school, and an output filter kids.out on the interface going out from its PortMaster to the school. The kids.in filter evaluates packets coming into the PortMaster from the school. The kids.out filter evaluates packets going out from the PortMaster to the school.
Figure 5-15 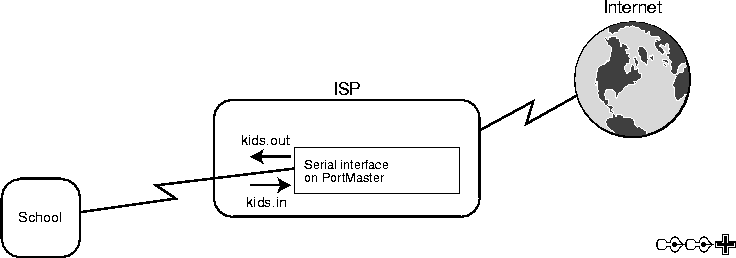 Filters Applied on the ISP's PortMaster Serial Interface
Filters Applied on the ISP's PortMaster Serial Interface
This example uses a variation of the method shown in Figure 5-15. Instead of both input and output filters, the example uses an input filter on the PortMaster interface from the school only. If a student requests access to sites not on the list, the filter denies the request packets from the student as the packets enter the ISP's PortMaster.
Figure 5-16 shows an example of a preconfiguration worksheet containing all the information needed to configure ChoiceNet for this example. Appendix D, "Preconfiguration Worksheets," has blank worksheets you can use to collect information before installing and configuring ChoiceNet.
Figure 5-16 Preconfiguration Worksheet for Example 2 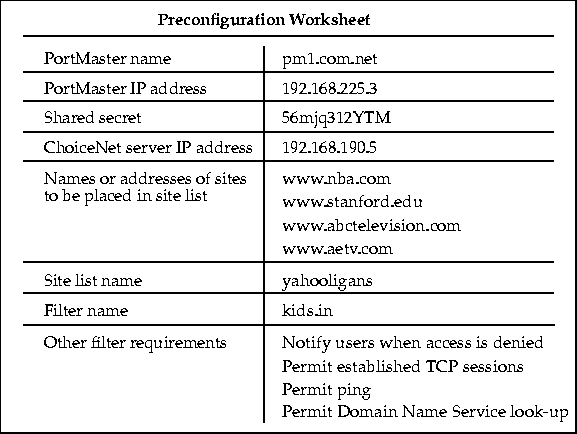
Follow these steps to configure ChoiceNet to limit student access (Example 2):
1. Add the ChoiceNet service in the /etc/services file on the ChoiceNet server:
choicenet 1647/udp filterd
|
2. On the ChoiceNet server in the /etc/choicenet/clients text file, do one of the following, but not both:
-
Define a ChoiceNet client name and shared secret:
#Client Name Shared Secret
#-------------------------------------------
pm1.com.net 56mjq312YTM
|
-
Define a ChoiceNet client IP address and shared secret:
#Client Name Shared Secret
#-------------------------------------------
192.168.225.3 56mjq312YTM
|
3. On the PortMaster, specify the address of the ChoiceNet server and define the shared secret:
Command> set choicenet 192.168.190.5
Command> set choicenet-secret 56mjq312YTM
Command> save all
|
4. Create the /etc/choicenet/lists/yahooligans file on the ChoiceNet server:
www.nba.com
www.stanford.edu
www.abctelevision.com
www.aetv.com
|
The list contains the Yahooligans-provided sites, one per line. The list is much abbreviated in this example.
5. Resolve the names in the yahooligans list:
/etc/choicenet/buildlist yahooligans
|
6. Create the /etc/choicenet/filters/kids.in filter on the ChoiceNet server for the custom Yahooligans access:
permit tcp estab
permit udp dst eq 53
permit tcp dst eq 53
permit 0.0.0.0/16 =yahooligans tcp dst eq 80
permit icmp
deny log notify
|
7. Install the user notification pop-up on each user's PC or Macintosh, if desired.
Refer to Chapter 4, "Installing User Notification."
8. Associate the kids.in filter with individual users on the RADIUS server.
To associate the filter with user masumi, for example, define the Filter-Id reply item in masumi's RADIUS user entry as the filter name, stripped of the suffix .in:
masumi Auth-Type = System
Service-Type = Framed-User,
Framed-Protocol = PPP,
Framed-Address = 255.255.255.254,
Framed-Routing = None,
Framed-MTU = 1500,
Filter-Id = "kids"
|
When masumi dials in to the ISP's PortMaster, RADIUS will apply the kids.in input filter on the interface coming into the PortMaster from the school.
9. Start the filter daemon using the following command:
With this ChoiceNet filter in place, students at the school service can gain Web access to only the sites that are specified in the yahooligans list. The students can use only DNS, HTTP, and ICMP services.
When a student attempts to connect to a site that is not listed in the yahooligans list, or tries to access a service not listed, such as FTP, the notify keyword in the rule opens a pop-up window on the student's computer to inform the student that access is denied. Because of the log keyword in the rule, the failed access attempt is also logged to the auth.notice facility of the ISP PortMaster's loghost.
[Top] [Prev] [Next] [Bottom]
spider@livingston.com
Copyright © 1997, Lucent Technologies, Inc. All rights
reserved.
 If name resolution fails and you want to rebuild the list, the DBM file(s) for the
list must first be deleted.
If name resolution fails and you want to rebuild the list, the DBM file(s) for the
list must first be deleted.
 If name resolution fails and you want to rebuild the list, the DBM file(s) for the
list must first be deleted.
If name resolution fails and you want to rebuild the list, the DBM file(s) for the
list must first be deleted.

 Any packet that is not explicitly permitted by a filter rule is denied. However,
an empty filter permits everything. If you create a filter and apply it without defining
any rules, the filter will permit all packets.
Any packet that is not explicitly permitted by a filter rule is denied. However,
an empty filter permits everything. If you create a filter and apply it without defining
any rules, the filter will permit all packets.



 Filters Applied on the School's Office Router Ethernet Interface
Filters Applied on the School's Office Router Ethernet Interface
 Filters Applied on the School's Office Router Serial Interface
Filters Applied on the School's Office Router Serial Interface
 Filters Applied on the ISP's PortMaster Serial Interface
Filters Applied on the ISP's PortMaster Serial Interface
