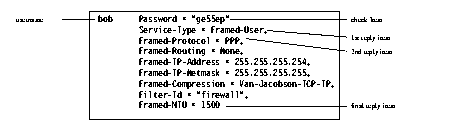
Table 4-2 User Profile Reply Items
|
Item
|
Options
|
Explanation
|
|---|
| Callback-Id
| Location name in double quotation marks (" ")
| Specify only for
Service-Type = Callback-Framed-User. Location must be in PortMaster location table.
|
| Callback-Number
| Phone number in double quotation marks (" ")
| Specify only for
Service-Type = Callback-Login-User.
|
| Filter-Id
| Filter name
| Filter name to be used for packet or access filtering on the interface.
|
| Framed-Compression
| None
| If this reply item is omitted, Van Jacobson TCP/IP header compression is used.
|
|
| Van-Jacobson-TCP-IP
| Van Jacobson TCP/IP header compression is used for the connection. Default.
|
| Framed-IP-Address
| IP Address
| The user's IP address.
|
| Framed-IP-Netmask
| Netmask
| The user's netmask.
|
| Framed-IPX-Network
| Dotted decimal IPX network number
| IPX network number.
|
| Framed-MTU
| Number
| Number of bytes in maximum transmission unit (MTU).
|
| Framed-Protocol
| PPP
| PPP is used for the connection.
Can also be used as a check item.
|
|
| SLIP
| SLIP is used for the connection.
|
| Framed-Route
| Destination IP address
| The IP address of the destination network.
|
|
| Gateway IP address
| The IP address of the gateway to the destination network.
|
|
| Metric
| The number of routing hops to the destination network. Also known as the hop count.
|
| Framed-Routing
| None
| Disables RIP on the interface.
|
|
| Broadcast
| The interface sends RIP updates.
|
|
| Listen
| The interface listens for RIP updates.
|
|
| Broadcast-Listen
| The interface sends and listens for RIP updates.
|
| Idle-Timeout
| In seconds
| Specifies the idle time limit for a session.
|
| Login-IP-Host
| IP address
| Address of the remote host.
|
| Login-Service
| Telnet
| Establishes a Telnet connection to the remote host.
|
|
| Rlogin
| Establishes an rlogin connection to the remote host.
|
|
| TCP-Clear
| Establishes a TCP clear connection to the remote host.
|
|
| PortMaster
| Establishes a connection to the remote host using the PortMaster login service.
|
| Login-TCP-Port
| TCP port number
| TCP port number of the Login-Service.
|
| Menu
| Menu name in double quotation marks (" ")
| Defines a menu in a user record. See Chapter 5, "Configuring RADIUS Menus."
|
| Port-Limit
| Number of B channels for ISDN Multilink PPP or Multilink V.120
| Specifies the maximum number of B channels a user can use.
|
| Session-Timeout
| In seconds
| Specifies the time limit for a session.
|
| Service-Type
| Administrative-User
| Grants user full access to all configuration commands.
|
|
| Callback-Login-User
| Calls user back and connects via Telnet, rlogin , PortMaster, or TCP-Clear login service.
|
|
| Callback-Framed-User
| Calls user back and establishes a framed connection (PPP or SLIP). Location must be specified in PortMaster location table.
|
|
| Framed-User
| User uses PPP or SLIP for the connection.
Can also be used as a check item.
|
|
| Login-User
| User connects via Telnet, rlogin , PortMaster, or TCP-Clear login service.
|
|
| NAS-Prompt-User
| Grants user limited access to commands (nonconfiguration only).
|
|
| Outbound-User
| User makes outbound connections via Telnet.
Can also be used as a check item.
|
| Termination-Menu
| Menu name in double quotation marks (" ")
| Menu to display after service is terminated.
|
![]() Lucent InterNetworking Systems recommends that you create a single user profile and test RADIUS authentication and authorization for that user. If the test is successful, create and test profiles representative of other user types before proceeding to create all your user profiles.
Lucent InterNetworking Systems recommends that you create a single user profile and test RADIUS authentication and authorization for that user. If the test is successful, create and test profiles representative of other user types before proceeding to create all your user profiles.