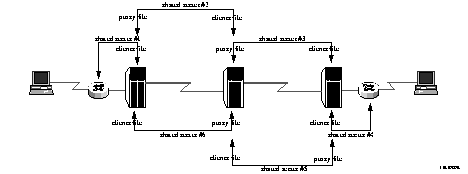
Figure 9-1 How Proxy Service Works 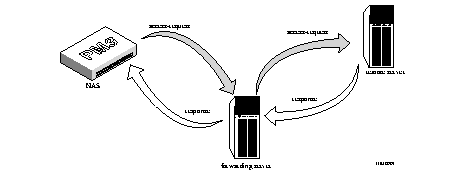
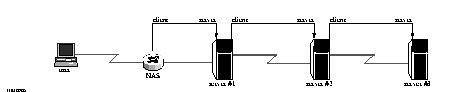
1. The NAS sends an accounting-request to the forwarding server.
2. The forwarding server writes the request to its accounting log.
3. The forwarding server forwards the request to the remote server.
4. The remote server logs the accounting-request and sends an accounting-response to the forwarding server.
5. The forwarding server sends the accounting response to the NAS.
Note ¯ ![]() If the request is forwarded across a chain of forwarding servers, the accounting records are stored on all servers in the chain.
If the request is forwarded across a chain of forwarding servers, the accounting records are stored on all servers in the chain.
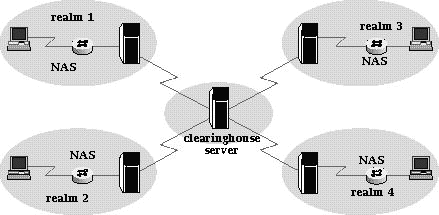
- A named realm is the part of a user login following the at sign (@). For example:
¯ If isolde@cornwall.net is the user login, cornwall.net is the realm.
¯ If sequoyah@cheroke e is the user login, cherokee is the realm.
A domain name is frequently used as the named realm to provide uniqueness.
- A numbered realm is a Called-Station-Id. You can establish a number for users to call if they need proxy service, and forward proxy requests based on the number called.
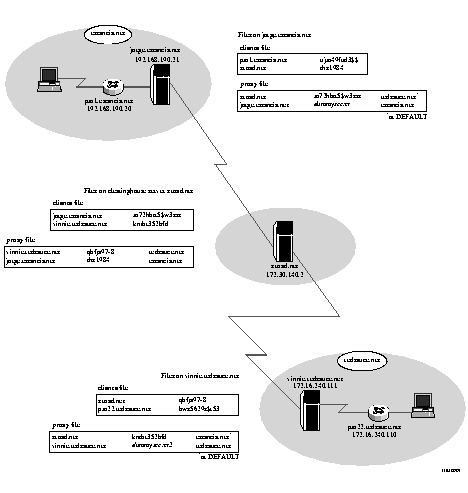
tracy.dog.net frtp67w3g3$1 2095559288
sanramon.dog.net xst1ru83vm7s3yhp 9255554613
Framed-IP-Address = 255.255.255.254,
Note ¯ ![]() Usernames with embedded @ s--such as tristram@cornwall.net --are treated as proxy realms.
Usernames with embedded @ s--such as tristram@cornwall.net --are treated as proxy realms.
Note ¯ ![]() RADIUS 2.1 currently supports the old username style, realm/ user. Lucent InterNetworking Systems might not support this style in future releases and recommends that you avoid such usernames. The at sign (@ ) always takes precedence over the slash sign (/ ). As a consequence, the radiusd daemon interprets a/b@c as user a/b in the named realm c. Lucent InterNetworking Systems strongly recommends avoiding such mixed usage.
RADIUS 2.1 currently supports the old username style, realm/ user. Lucent InterNetworking Systems might not support this style in future releases and recommends that you avoid such usernames. The at sign (@ ) always takes precedence over the slash sign (/ ). As a consequence, the radiusd daemon interprets a/b@c as user a/b in the named realm c. Lucent InterNetworking Systems strongly recommends avoiding such mixed usage.
Note ¯ ![]() The Lucent RADIUS Proxy-State attribute consists of an opaque sequence of octets and is subject to change without notice. The attribute value is only meaningful to the server that sent the attribute.
The Lucent RADIUS Proxy-State attribute consists of an opaque sequence of octets and is subject to change without notice. The attribute value is only meaningful to the server that sent the attribute.