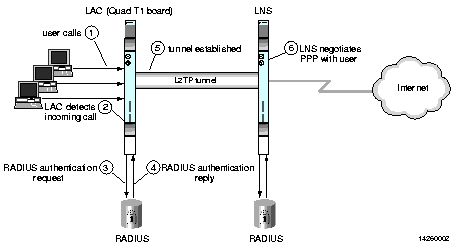
Follow this procedure to set up an entire PortMaster 4 as a LAC:
1. Set the view to the first slot with an installed line board.
Command> set view Slotnumber
2. Configure the line board to inherit its LAC configuration from the manager module.
Command Slotnumber> set l2tp noconfig lac
3. Save the configuration and reset the slot.
Command Slotnumber> save all
Command Slotnumber> reset slotSlotnumber
4. Repeat Steps 1 through 3 for all remaining line boards.
5. Set the view to the manager module and globally enable the LAC functionality.
Command Slotnumber> set view 4
Command> set l2tp lac enable
6. Save the changes and reboot the PortMaster for the changes to take effect.
Command> save all
Command> reboot
To globally disable the LAC functionality on a PortMaster, set the view to the manager module and enter the following commands:
Command> set l2tp disable lac
Command> save all
Command> reboot
When you reboot the PortMaster, all line boards set with the noconfig keyword inherit the disable setting from the manager module. If you do not want all line boards to automatically inherit the disable setting upon reboot, you can alternatively enter the following commands on the manager module:
Command> set l2tp noconfig
Command> save all
Command> reboot
Now when you reboot the PortMaster, line boards retain their own configurations. This approach is useful if you want to add new line boards to the PortMaster with configurations other than for L2TP, or if you want to configure LAC and LNS functionality on the same PortMaster.
Refer to the PortMaster 4 Command Line Reference for more details about commands, and for ComOS release-specific versions of L2TP commands.
Note ¯  An entire PortMaster 4 cannot operate as both an LNS and a LAC at the same time. You can configure one board as a LAC and another board as an LNS on the same PortMaster 4, but these two boards must function as end points for independent tunnels.
An entire PortMaster 4 cannot operate as both an LNS and a LAC at the same time. You can configure one board as a LAC and another board as an LNS on the same PortMaster 4, but these two boards must function as end points for independent tunnels.
![]() You must be running RADIUS 2.1 or later to configure L2TP. Earlier versions of RADIUS do not support call-checking.
You must be running RADIUS 2.1 or later to configure L2TP. Earlier versions of RADIUS do not support call-checking.