Inside RADIUS
RADIUS 2.0.1 is the latest version of the Security and Accounting Server. The following section gives a detailed description of the RADIUS server and accounting modules.
The RADIUS software is organized in a hierarchical structure with various files and directories. These files and directories are grouped into the raddb (RADIUS database) directory as follows:
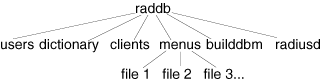
The following sections describe each of the above components.
1) users file
users file is a text file that contains user profiles. users file resides in the raddb directory of the RADIUS server. The user profile contains the security and configuration information for each user. The first field of the user profile contains the user's name. The user's name can be up to 63 characters. The next field specifies the authentication method for that user. An expiration date for the user's password may also be specified following the authentication type. The following entries illustrate a user record for a PPP session with a specified address:
Pkim Password = "testing", Expiration = "24 Dec 1996" Service-Type = Framed-User, Framed-Protocol = PPP, Framed-Address = 172.16.3.33, Framed-Netmask = 255.255.255.0, Framed-Routing = Broadcast-Listen, Filter-Id = "std.ppp", Framed-MTU = 1500, Framed-Compression = Van-Jacobsen-TCP-IP
When a user is logging into the network via the PortMaster, this user name will be parsed from the top down in the users file. If there is a match between user's name and password, that user will be authenticated. If a matching username/password pair cannot be found, the RADIUS server will try to match that user with the DEFAULT user profiles. The DEFAULT user profiles are defined at the end of the users file.
2) dictionary file
dictionary is a text file that contains all parameters that can be used to define a user profile. In other words, in order for a parameter to be correctly identified in the user profile, this parameter must be specified in the dictionary file. All transactions in the user profile are composed of attribute and value pairs. In the previous example for user Pkim, words on the left of the = sign are attributes and words on the right are values. RADIUS supports four service types, four login services, and three authentication types. The four user service types are as follows:
- Login-User designates telnet or rlogin sessions
- Framed-User designates PPP or SLIP sessions
- Dialback-Login-User designates dialback session for telnet or rlogin users
- Dialback-Framed-User designates dialback session for PPP or SLIP users
The four login services are as follows:
- Telnet indicates that the login is a telnet session
- Rlogin indicates that the login is remote login
- PortMaster indicates that the PortMaster process in.pmd is running on the Login-Host. The in.pmd process allows the PortMaster to multiplex incoming users onto the host with one TCP stream.
- TCP-Clear provides a NetData channel for special purposes.
The three authentication types are as follows:
- Local: Local indicates that the password is in the RADIUS users file.
The following example illustrates a user profile with the local password entry:
Peg Password = "ge55gep"
- UNIX: UNIX indicates that the password is a UNIX password file. The RADIUS server will authenticate the user based on the password file of the specified UNIX host. If the Network Information Service (NIS) is used, the password table in the NIS or NIS+ database will be used.
The following example illustrates a user profile with the UNIX password entry:
Seg Password = "UNIX"
- SecurID: SecurID is a new feature in RADIUS SecurID is an authentication method based on Security Dynamics' time-synchronization token and Personal Identification Number (PIN).
The following example illustrates a user profile with the SecurID entry:
kimf Auth-Type = SecurID
- Other Authentication Type
In addition to the above authentication types, a user profile can be configured to use either PAP or CHAP authentication. For example, in the following user profile, the Framed-Protocol attribute defined on the same line as the Password indicates that PAP authentication will be used. The subsequent Framed-Protocol indicates that this is a PPP session.
DEFAULT Password = "UNIX", Framed-Protocol = PPP User-Service-Type = Framed-User, Framed-Protocol = PPP, Framed-Address = 192.9.200.130, Framed-Compression = None, Framed-MTU = 1500
If CHAP authentication is preferred, PAP should be disabled on the PortMaster using the set pap off command and the password = "UNIX" cannot be used.
3) clients file
The clients file contains the RADIUS clients' names and secret passwords. When an authentication request is sent from a PortMaster, the clients file will be consulted to verify the validity of the PortMaster. The secret in the clients file on the RADIUS server in conjunction with the secret defined on the PortMaster form the handshaking for communication between the RADIUS server and clients.
4) menus directory
This is a new feature of RADIUS. The menus directory contains the files that can be used to define login services in the user profile. Menu is an attribute defined in the dictionary file. The attribute/value pair for this feature are defined as follows:
Menu = "filename"
A menu file accommodates up to 2Kbytes of data and can contain any printable ASCII characters. A menu can be nested within another menu or it can be a single-level menu. A menu file includes the "menu" and "end" keywords to indicate the start and end point of the display. The menu file is terminated with an "EXIT" keyword. Since the menu file is in text format, it permits administrators to compose the display messages without any knowledge of programming or scripting. The menu file is displayed to the user after authentication.
5) builddbm utility
RADIUS supports DBM lookup on all platforms without recompilation, by using the -b flag with radiusd. The builddbm utility program turns the flat text users file into a UNIX DBM file for faster lookups. This feature is mainly used for a large site in which the users file contains thousands of user profiles. When building the database for the users file with builddbm, it generates the users.dir and users.pag files which is used by radiusd. The syntax for builddbm is as follows:
builddbm users
6) radiusd process
radiusd is a UNIX daemon that runs on the RADIUS server to communicate with its clients. This process employs the UDP port 1645. Furthermore, the radiusd process is an authentication mechanism of RADIUS. The radiusd process has several options. These options are as follows:
-d specifies an alternate directory for RADIUS. The default directory is /etc/raddb.
-b is used when the RADIUS users database is built with the builddbm utility.
-l option indicates the name and location of the RADIUS logfile.
-x is for debugging.
-a specifies an alternate directory for the accounting server. The default is /var/adm/radacct.
-s is used when RADIUS is run in a single-user mode.
-v displays the version of the server.
What's New In RADIUS
RADIUS is easier to use than previous versions. It includes a number of enhancements to existing features and integrates SecurID, a third party authentication technology.
RADIUS implements the following new features:1. SecurID
SecurID authentication is based on Security Dynamics' SecurID token technology. SecurID uses Security Dynamics' patented time-synchronization that generates pseudo-random code on the token cards. There are three types of SecurID token cards that can be used to authenticate users with RADIUS: the standard SecurID card, the SecurID key fob card, and the SecurID PINPAD card. These cards display a random number every 60 seconds. When a user is dialing into the network, he/she must enter a valid PASSCODE comprised of two factors:
- The memorized personal identification number (PIN)- The code currently displayed on the SecurID card
In addition to the RADIUS logfile, SecurID also generates an audit trail that can only be viewed by the site's Security Administrator. The attribute/value pair for SecurID are defined as follows:
Auth-Type = SecurID2. Menu Display
Refer to "menus directory" on page three.
3. Prefix and Suffix
The Prefix and Suffix features are designed to provide flexibility and simplicity for RADIUS administration. Prefix and Suffix are used for UNIX and SecurID authentication. The Prefix and Suffix can be any string of characters. The Attribute/Value pairs for the Prefix and Suffix are defined as follows:
Prefix = "any string characters"Suffix = "any string characters"
Prefix or Suffix are useful in specifying the type of user account; for example, P for PPP account, S for SLIP account, C for CSLIP account, or T for Telnet account. When a Prefix is defined for the DEFAULT profile, the user must enter the Prefix character preceding his/her user name every time the network is dialed. Similarly, when a Suffix is defined for the DEFAULT profile, the user must specify the Suffix string when logging in. The greatest benefit that Prefix and Suffix offers to the ISP is the capability to provide different account types without increasing RADIUS administration. For example, with the DEFAULT records defined below, the ISP can add account types to its new and existing user base without modifying the users file:
DEFAULT Password = "UNIX", Prefix = "P" Service-Type = Framed-User, Framed-Protocol = PPP, Framed-IP-Address = 101.2.12.2, Framed-Compression = None, Framed-MTU = 1500 DEFAULT Password = "UNIX", Prefix = "S" Service-Type = Framed-User, Framed-Protocol = SLIP, Framed-IP-Address = 101.3.12.3, Framed-Compression = None, Framed-MTU = 1006 DEFAULT Password = "UNIX", Prefix = "C" Service-Type = Framed-User, Framed-Protocol = SLIP, Framed-IP-Address = 101.3.12.1, Framed-Compression = Van-Jacobsen-TCP-IP, Framed-MTU = 1006 DEFAULT Password = "UNIX", Prefix = "T" Service-Type = Login-User, Login-IP-Host = 205.104.1.101, Login-Service = Telnet, Login-Port = 23
With the above DEFAULT records, the same user can log in using four different accounts. When a user is dialing into the network, the user's name and password will be verified in the UNIX password file.
When a Prefix or Suffix is defined for a user name, when a user is dialing into the network, only the user name must be entered, the Prefix or Suffix string will be stripped off.
For example:Tkimf Auth-Type = SecurID, Prefix = "T" Service-Type = Login-User, Login-IP-Host = 255.255.255.255, Login-Service = Telnet, Login-Port = 23
In this example, the user kimf and her password will be verified in the SecurID database. When kimf dials into the network, her login ID would be kimf and her password is a PIN number followed by the SecurID card display. The Prefix T will be removed.
elainePPP Password = "UNIX", Suffix = "PPP" Service-Type = Framed-User, Framed-Protocol = PPP, Framed-IP-Address = 101.2.12.2, Framed-Compression = None, Framed-MTU = 1500
In this example, the user elaine and her password will be verified in the UNIX password file. When elaine dials into the network, her login ID would be elaine; the Suffix PPP will be removed.
4. RADIUS users databaseRefer to "builddbm" utility on page four.
5. New RADIUS Attributes RADIUS implements several new attributes. These new attributes and their functions are described as follows:
Idle-Timeout
Idle-Timeout indicates the time limit for an idle session. The time of this attribute can be expressed in seconds and ranges from 120 seconds (2 minutes) to 14,400 seconds (4 hours).
Session-Timeout
If RADIUS returns a session time limit using the new Session-Timeout attribute, the user will be disconnected when the time limit is reached regardless of what the user is doing. The time of this attribute can be expressed in seconds and can be up to one year long.
Port-Limit
PortMasters can be configured to allow a maximum number of ports on a per-user basis. If left unconfigured, port limits will not be imposed. If a port limit is set, the user will be limited to that maximum number of ports on the PortMaster for Multilink V.120 and Multilink PPP sessions for ISDN. This feature can be used to restrict which users can have service greater than 64 Kbps. Per user port limits can be set in either the local user table or user profile in RADIUS.
NAS-Port-Type
The NAS-Port-Type attribute indicates the port type specification. This attribute is useful for specifying the ports in the PortMaster units that have a mixture of asynchronous, synchronous, and ISDN. This attribute is also implemented in RADIUS accounting to keep track of the login service.
RADIUS Accounting
Similar to authentication, RADIUS accounting element uses a client-server architecture. The radiusd process includes an accounting server. RADIUS accounting uses UDP port 1646. The accounting server can be run on the same host as the RADIUS authentication and authorization server, or may be run on a separate UNIX host. Once the accounting server is defined on the PortMaster and a user is authenticated, the accounting information for that user is appended to the file:
/var/adm/radacct/<PortMaster_name>/detail
The accounting records provide a wealth of information about the status of the users. One of the greatest benefits of accounting records for use in billing purposes is the length of login sessions and the type of port (ISDN or Asynchronous). Following are some samples of RADIUS accounting records:
Wed May 8 10:51:12 1996Acct-Session-Id = "F400020E"
User-Name = "Pandy"
Client-Id = 172.16.1.21
Client-Port-Id = 12
NAS-Port-Type = ISDN
Acct-Status-Type = Start
Acct-Authentic = RADIUS
Called-Station-Id = "4856702"
Calling-Station-Id = "5104856754"
User-Service-Type = Framed-User
Framed-Protocol = PPP
Framed-Address = 172.16.93.1
Acct-Delay-Time = 0
Wed May 8 11:37:30 1996
Acct-Session-Id = "F400020C"
User-Name = "pmtest"
Client-Id = 172.16.1.21
Client-Port-Id = 14
NAS-Port-Type = ISDN
Acct-Status-Type = Stop
Acct-Session-Time = 5450
Acct-Authentic = Local
Acct-Input-Octets = 110509
Acct-Output-Octets = 263779
Called-Station-Id = "4856704"
User-Service-Type = Framed-User
Framed-Protocol = PPP
Framed-Address = 172.16.131.5
Acct-Delay-Time = 0
There are various ways to extract information from accounting records with customized scripts. However, for billing purposes, provides a script to display the user name, time usage, number of uses, calculate charges,and the date and time stamp as follows. The ISP can bill the users based on this information.
pmtest 3:21:40 4 0 Wed May 8 11:37:30 1996
New Accounting Attributes
Called-Station-Id and Calling-Station-Id
On ISDN dial-up connections (where provided by the ISDN carrier) these attributes can be used to track physical origination of ISDN calls.
Acct-Input-Octets and Acct-Output-Octets
These two attributes are generated in the Stop records.
NAS-Port-Type
As indicated above, RADIUS implements the NAS-Port-Type attribute for authentication and accounting. The NAS-Port-Type indicates whether the port type is ISDN or asynchronous. For ISPs that provide both ISDN and asynchronous services with a different pricing structure, this can provide helpful information so that users can be billed accordingly.
Conclusion
RADIUS is included on the Total Access CD-ROM free of charge for all new Lucent customers.